Think of a hard drive destruction certificate as the official death certificate for your company's sensitive data. It's a legally binding document that proves storage media has been physically destroyed, making the information on it permanently unrecoverable. For any business owner or IT manager in a data-heavy sector, this certificate is your definitive proof of compliance and your best defense against data breach liability.
The Role of a Destruction Certificate in Your ITAD Strategy
When your business retires old computers, servers, or storage arrays as part of an office cleanout, just hitting 'delete' isn't nearly enough to protect you. Lingering data can be a goldmine for cybercriminals and a massive liability for your organization. A hard drive destruction certificate transforms the abstract concept of "data security" into a tangible, auditable record. It serves as the final, crucial step in your IT Asset Disposition (ITAD) process.
For IT managers and corporate sustainability leaders, this document is far more than just paperwork. It's an essential tool for risk management and a clear demonstration of due diligence. In the event of an audit or a security incident investigation, this certificate proves your company took the right steps to safeguard confidential information.
Why This Document is Non-Negotiable
A professionally issued certificate of destruction is your shield against severe regulatory penalties. Data privacy laws like HIPAA, GDPR, and FACTA don't just recommend secure data disposal; they mandate it. Failure to provide proof of destruction can result in fines that can cripple a business.
A certificate of destruction plays several critical roles in safeguarding your business. It's the tangible proof that bridges the gap between the physical act of destruction and your legal and regulatory obligations.
Key Functions of a Hard Drive Destruction Certificate
| Function | Business Impact |
|---|---|
| Legal Compliance | Provides necessary documentation to satisfy auditors and prove adherence to strict data privacy laws. |
| Risk Mitigation | Serves as concrete evidence in legal proceedings, significantly reducing liability if a breach is ever alleged. |
| Brand Protection | Demonstrates a firm commitment to data security, protecting your company's reputation and maintaining customer trust. |
| Chain of Custody | Creates an unbroken, auditable trail from the moment an asset leaves your possession to its final destruction. |
This documentation is what makes your IT equipment disposal process defensible and complete, ensuring every loose end is tied up.

Integrating Security with Social Responsibility
Partnering with a social enterprise like Reworx Recycling for your secure data destruction needs adds another layer of value. We ensure your data is completely eliminated according to the highest industry standards and provide an official certificate for your records.
By choosing a donation-based recycling partner, you turn a necessary security expense into a positive community impact. Your retired assets are not only securely processed but also contribute to digital inclusion and workforce development programs.
This approach allows your organization to meet its security and compliance obligations while simultaneously advancing corporate social responsibility (CSR) goals. You get the peace of mind that comes with a certified destruction process, and you contribute to a more sustainable and equitable future.
To get a clearer idea of what this document includes, you can view a comprehensive destruction certificate template on our site.
What Makes a Destruction Certificate Audit-Proof
Let's be clear: not all documents labeled "Certificate of Destruction" are created equal. When you're facing a compliance audit or a legal question, a flimsy, incomplete certificate might as well be blank paper. It offers zero protection.
An audit-proof hard drive destruction certificate is a different beast entirely. It's meticulously detailed, fully traceable, and built to be legally defensible. It leaves absolutely no room for doubt or ambiguity. Think of it as the unbreakable final link in your chain of custody, proving not just that some hardware was destroyed, but that specific assets with specific serial numbers were verifiably and permanently gone. That level of detail is what turns a simple receipt into a powerful compliance shield.

Core Components of a Legally Defensible Certificate
To stand up to serious scrutiny, a destruction certificate has to contain a few non-negotiable elements. These are the pillars that give it legal weight. An auditor will scan for these fields first to verify the integrity of your whole IT asset disposition (ITAD) process.
A truly solid certificate will always have:
- A Unique Certificate ID: A tracking or serial number that makes the document one-of-a-kind and easy to cross-reference in your asset management system.
- Your Company's Information: The full legal name and address of your organization—the owner of the assets.
- Vendor's Information: The name, address, and contact details of the certified ITAD partner, like Reworx Recycling, that handled the destruction.
- Date of Destruction: The exact date the physical destruction happened, which is crucial for building an accurate timeline.
Without these foundational details, the document loses all authority. It can't provide the clear, auditable trail you need.
The Critical Role of Serial Numbers
If there's one thing that makes a destruction certificate truly audit-proof, it's a detailed list of individual asset serial numbers. A certificate that just says "50 hard drives destroyed" is fundamentally useless from a compliance standpoint because it doesn't prove anything specific.
An auditor needs to be able to pick a serial number from your original inventory list and find its exact match on the destruction certificate. This one-to-one connection is the absolute cornerstone of a defensible chain of custody.
At Reworx Recycling, we understand this is a deal-breaker. Our process guarantees that every single drive, whether it comes from a server, a laptop, or medical equipment, is individually scanned. Its serial number is captured and recorded on the final certificate. This meticulous tracking gives you the granular proof required for even the strictest compliance standards.
Documenting the Method of Destruction
How a drive was destroyed is just as important as the fact that it was destroyed. Vague descriptions like "data destruction" won't cut it for an auditor. An audit-proof certificate has to specify the exact method used, because different rules apply to different types of media and security levels.
The certificate should clearly state if the media was destroyed via:
- Shredding: Physically annihilating the drive into tiny, irrecoverable fragments. The document might even specify the shred size (e.g., 2mm) for high-security jobs.
- Crushing/Pulverizing: Using immense force to mangle, bend, and smash the drive platters beyond any hope of recovery.
- Degaussing: Blasting the media with a powerful magnetic field to erase the data before the physical destruction occurs.
This level of specificity is vital for showing you're compliant with standards like the NIST 800-88 Guidelines for Media Sanitization. By documenting the method, you're not just proving you destroyed an asset; you're proving you did it right, meeting or exceeding federal guidelines.
You can dive deeper into how these and other rules shape responsible recycling by exploring various e-waste certification standards. Understanding the broader benefits of meeting security compliance helps put every detail on your certificate into context. This knowledge solidifies your defense against potential liabilities and strengthens your organization's entire security posture.
The Real Cost of Not Having Proof of Destruction
What happens when a critical hard drive leaves your facility, and you have no way to prove it was properly destroyed? For many businesses, the answer is a dangerous unknown. Skipping the step of securing a hard drive destruction certificate is like leaving your company’s front door unlocked—you might be fine for a while, but the potential consequences are catastrophic.
Thinking of this certificate as a mere expense is a critical mistake. It's actually an essential insurance policy. Without this tangible proof, your business is left exposed to severe financial penalties, draining legal battles, and a permanent stain on its reputation. It’s the one document that stands between your company and accusations of negligence if a data breach ever occurs.
The Financial Fallout of Non-Compliance
The financial risks that come with improper data disposal are far from theoretical. Regulatory bodies are hitting organizations with increasingly harsh penalties for failing to protect sensitive information. A single lost or unaccounted-for hard drive containing customer data or protected health information (PHI) can trigger fines that easily reach into the millions.
Let's look at the penalties under major data privacy laws:
- HIPAA (Health Insurance Portability and Accountability Act): Violations can lead to fines up to $1.5 million per year for each category of violation. The lack of a destruction certificate makes it nearly impossible to defend against claims of willful neglect.
- GDPR (General Data Protection Regulation): For companies doing business with EU citizens, penalties can be as high as €20 million or 4% of global annual revenue, whichever is greater. Proving data was properly erased is a core requirement.
- FACTA (Fair and Accurate Credit Transactions Act): This act mandates the proper disposal of consumer credit information. Failure to comply can lead to federal and state enforcement actions, as well as civil liability.
These aren't just numbers on a page; they are business-ending threats. The cost of a professional, certified destruction service from a partner like Reworx Recycling is a minuscule fraction of the potential fines, making it an undeniable strategic investment.
Reputational Damage and Loss of Trust
Beyond the immediate financial hit, the reputational damage from a data breach can be even more costly and difficult to repair. When customers entrust their data to you, they expect it to be protected throughout its entire lifecycle—from creation to final destruction.
A data breach resulting from improper IT asset disposal sends a clear message to your clients, partners, and the public: your organization cannot be trusted with sensitive information. This loss of confidence can lead to customer churn, broken partnerships, and a devalued brand that takes years to rebuild.
Market analytics show a surge in demand for data destruction services, fueled by global data privacy laws and the dramatic increase in data breach incidents. In the U.S. alone, reported data breaches grew significantly in recent years, affecting billions of people worldwide. The financial impact is staggering; one ransomware attack on a healthcare company resulted in sensitive patient data being compromised nationwide with recovery costs reaching billions. You can explore more research on the growing data destruction market to understand the scale of this issue.
Ensuring proper data destruction is part of a broader strategy for data protection, which also includes robust disaster recovery planning. By working with a certified vendor that provides a detailed hard drive destruction certificate, you're making a public commitment to security. You can learn more about why secure data destruction is crucial in our detailed guide. This protects your bottom line and reinforces the integrity of your brand in a marketplace that is increasingly wary of data security failures.
Establishing a Secure Chain of Custody for Your IT Assets
A hard drive destruction certificate is the final piece of the puzzle, but its real value hinges on the strength of the process that comes before it. This process is called the chain of custody—a documented, unbroken trail that tracks your sensitive IT assets from the moment they leave your sight to their final, verified destruction.
Without a solid chain of custody, a certificate is just a piece of paper. But with one, it becomes an ironclad legal defense.
This paper trail is what eliminates security gaps and proves you’ve done your due diligence. It ensures no device can mysteriously "fall off the back of the truck" or get misplaced in a warehouse, leaving your company’s data completely exposed. Every step is documented, and every handover is signed for, creating a seamless record of responsibility.
Building Your Unbreakable Chain of Custody
A truly secure chain of custody isn't complicated; it's built on clear, repeatable steps that leave zero room for error. Think of it as a systematic approach to asset control that your IT team can put into practice right away. The goal is to create a process so transparent you can pinpoint the location and status of any retired asset at any given moment.
Here are the practical, essential best practices for building that process:
- Serialized Asset Logging: Before a single piece of equipment is moved, create a detailed inventory. Log the asset type (like a laptop or server), manufacturer, model, and—most importantly—the unique serial number of every device holding data.
- Secure, Sealed Transport: Devices should be placed into sealed, tamper-evident containers before they even leave your facility. These containers need to be locked and labeled, preventing anyone from getting unauthorized access during transit.
- Documented Handover Protocols: Every single time the assets change hands—from your IT staff to the transport team, or from them to the destruction facility—it must be documented. Signatures, dates, and times are non-negotiable to confirm who is responsible at every stage.
This meticulous approach is the foundation of any defensible IT asset disposition strategy. For a deeper dive into all the components involved, our guide on what IT asset disposition is offers a complete overview.
To help you get started, here is a simple checklist you can use to track your assets through the entire disposition process.
Chain of Custody Checklist for IT Asset Disposition
| Step | Action Required | Verification Method |
|---|---|---|
| 1. Internal Logging | Create an inventory list with serial numbers for all devices. | Internal inventory spreadsheet or asset management software. |
| 2. Secure Collection | Place all assets in locked, tamper-evident containers. | Photographs of sealed containers; signed collection form. |
| 3. Vendor Pickup | Have the ITAD vendor verify and sign for the collected assets. | Signed Bill of Lading matching your internal inventory list. |
| 4. Secure Transit | Confirm the vendor uses locked, GPS-tracked vehicles. | Ask for proof of GPS tracking in the vendor service agreement. |
| 5. Facility Arrival | Receive notification that assets have arrived at the secure facility. | Signed receiving report from the destruction facility. |
| 6. Final Reconciliation | Match the final destruction report serial numbers to your original list. | Certificate of Destruction with a complete, serialized list. |
Following these steps methodically closes any potential security loopholes and provides a complete, auditable record from start to finish.
The Role of a Professional ITAD Partner
Let's be honest: managing a flawless chain of custody internally can be a huge logistical headache. This is where a certified partner like Reworx Recycling becomes indispensable. We’re trained to not just perform secure data destruction but to uphold the integrity of the chain of custody from the moment we arrive at your door.
Our secure process includes:
- On-site asset scanning to verify your inventory list against the physical hardware.
- Use of locked, GPS-tracked vehicles for secure transport to our facility.
- Documented check-in procedures at our secure, access-controlled facility.
- A final, serialized report that reconciles the initial inventory with the destroyed assets.
This infographic shows what can happen when a secure chain of custody fails and proof of destruction isn't available.
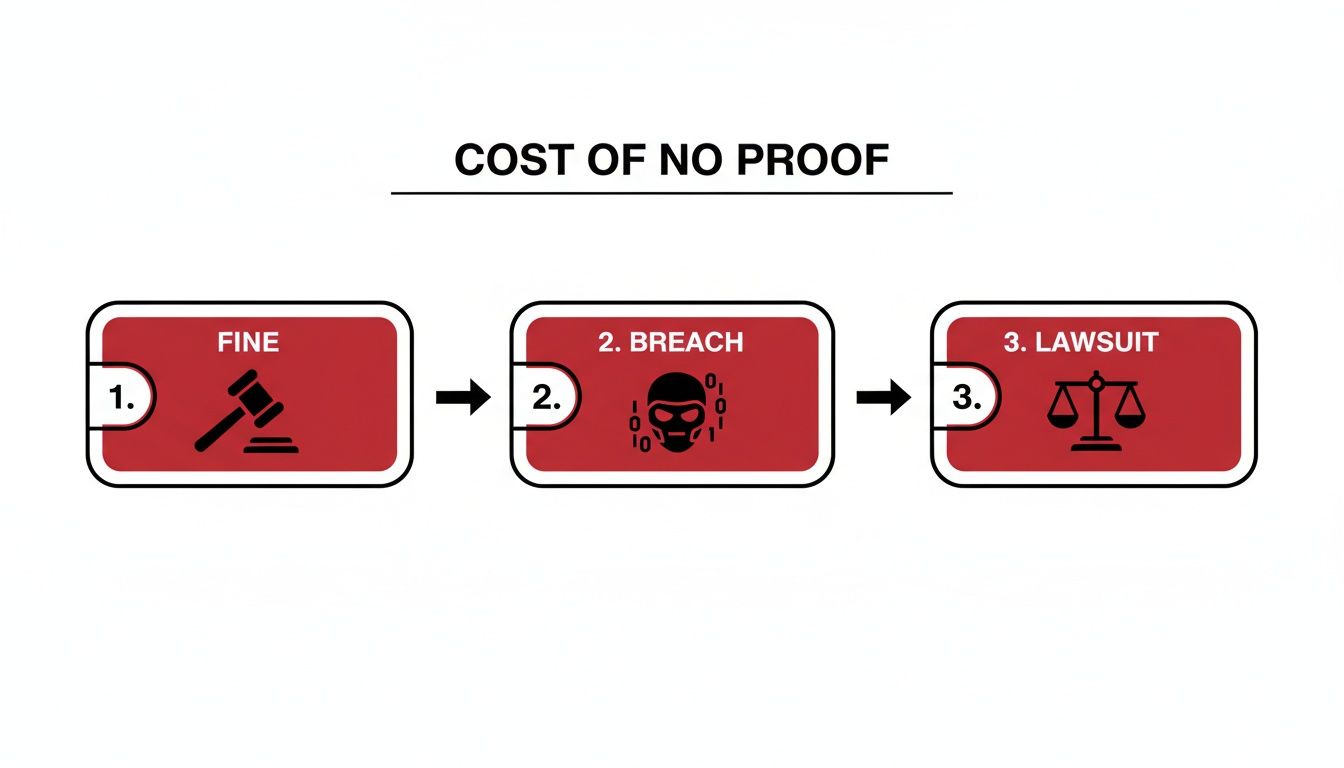
As you can see, a single gap in your documentation can snowball into major legal and financial disasters, starting with regulatory fines and escalating to breach notifications and lawsuits.
By entrusting your retired IT equipment to Reworx Recycling, you aren’t just outsourcing a task; you’re integrating a team of security professionals into your compliance framework. We provide the expertise, infrastructure, and paperwork needed to ensure your chain of custody is airtight. This lets you focus on your core business, confident that your data security and legal obligations are being handled with the highest level of care.
How to Choose a Certified Data Destruction Partner
Picking the right partner for your IT Asset Disposition (ITAD) is a huge decision. It directly affects your data security, your compliance standing, and even your company’s reputation. A true partner does more than just shred hard drives; they deliver a secure, auditable process that shields you from risk. When you choose correctly, the hard drive destruction certificate you receive is a rock-solid guarantee, not just a piece of paper.
This isn’t about finding the lowest price—it's about digging into a vendor’s credentials, processes, and values. You can't afford to cut corners here. The partner you select becomes the final line of defense for your most sensitive information, and a bad choice can undermine every security measure you’ve put in place.
The demand for secure hard drive destruction is exploding, driven by tough data privacy laws and the ever-present threat of a breach. The global market, recently valued at around USD 1.65 billion, is projected to hit USD 5.05 billion within a decade. This surge is particularly strong in North America, where regulations like HIPAA and CCPA make certified destruction a must-have for businesses in finance, healthcare, and IT. You can see the data behind these market trends and understand what’s fueling the need for these services.
Look for Verifiable Industry Certifications
Industry certifications are your best shortcut to finding a competent and committed vendor. Think of them as a seal of approval from a trusted third party, confirming that a provider meets strict standards for data destruction, security, and environmental responsibility.
When you're vetting potential partners, these certifications should be at the top of your checklist:
- NAID AAA Certification: This is the gold standard for data destruction. It means the vendor has passed surprise, in-depth audits covering everything from employee background checks and facility access to the destruction process itself. A NAID AAA certified partner ensures your data is secure every step of the way.
- R2 (Responsible Recycling) Certification: While NAID is all about data security, R2 focuses on doing right by the planet. An R2 certified vendor guarantees that once your drives are destroyed, the leftover materials are recycled safely and ethically, keeping hazardous e-waste out of landfills.
These certifications give you a clear baseline for quality and trust, making it much easier to narrow down your options.
The Power of Choosing a Social Enterprise
After checking for certifications, think about the vendor’s business model and how it aligns with your company's own values. This is where partnering with a social enterprise like Reworx Recycling gives you a unique edge. We offer the same high-level, certified data destruction you'd expect from any top ITAD provider, complete with a fully compliant hard drive destruction certificate.
The difference is that your partnership with us goes further. By choosing our donation-based model, you transform a standard operational necessity into a powerful act of corporate social responsibility (CSR).
Instead of just checking a compliance box, your IT asset disposal becomes a direct investment in the community. The value we recover from reusable components helps fund digital inclusion programs and provide workforce development opportunities, creating a positive ripple effect. Our guide on selecting a reliable e-waste recycling partner dives deeper into how you can balance security with sustainability.
This approach lets your business achieve flawless data security while making a real social impact. It's a strategic move that benefits your IT, compliance, and sustainability teams all at once, proving that doing good is also good for business.
Your Questions About Destruction Certificates Answered
Once you get the basics down, you’ll find that specific, practical questions pop up. It's totally normal. Here are some of the most common questions IT managers and business owners ask about the hard drive destruction certificate and how it fits into a real-world compliance plan.
How Long Should We Keep a Hard Drive Destruction Certificate?
This is a great question, but there isn’t a single, one-size-fits-all answer. No federal law sets a universal retention period, so the right answer really hinges on your industry and the specific rules you have to play by. Your retention policy should be a deliberate decision, not just something you figure out later.
For instance, if you're in healthcare and dealing with HIPAA, you absolutely must hold onto records related to Protected Health Information (PHI) disposal for at least six years. Other industries might be looking at different timelines based on regulations like Sarbanes-Oxley (SOX) or GDPR.
The safest bet? Just align the retention period with your company's official data retention policy. Honestly, with the penalties for non-compliance being so steep, a lot of organizations just decide to keep these certificates forever. Modern digital certificates, like the ones we provide at Reworx Recycling, make it simple to archive them securely for as long as you need.
Is a Certificate from Data Wiping Software Good Enough?
Data wiping, or data sanitization, is a perfectly valid way to make data unreadable according to NIST guidelines. But whether it's "good enough" for you comes down to how sensitive your data is and how much risk you’re willing to accept. A software certificate proves one thing: that a wiping program was started and finished on a drive.
It doesn't prove the drive itself is gone.
If you handle highly sensitive information—think Personally Identifiable Information (PII), PHI, financial records, or your company's secret sauce—physical destruction is the only way to be 100% certain that data can never be recovered. A wiped drive is still a physical object. It can be lost, stolen, or potentially have data pulled from it with sophisticated forensic tools.
A software certificate proves the process ran; a hard drive destruction certificate proves the media no longer exists. The latter offers a far superior level of security and a much stronger legal defense if a data breach ever happens.
When the stakes are high, physical destruction gives you absolute certainty. It's why it remains the go-to choice for sensitive data.
What if a Certificate Is Missing Asset Serial Numbers?
A certificate of destruction without an itemized list of every single asset's serial number is a massive compliance red flag. It completely breaks the chain of custody right where it matters most, making the document pretty much useless for an audit.
Think about it: without specific serial numbers, you can't prove a direct link between that one specific laptop in your inventory and its final destruction. If an auditor or investigator comes asking about a particular hard drive, all you can prove is that a batch of devices was processed. That's not good enough.
That kind of ambiguity is a non-starter for auditors. Always, always insist that your ITAD partner provides a serialized certificate. Any reputable, certified vendor like Reworx Recycling knows this is a non-negotiable part of a compliant and legally defensible process.
Can We Create Our Own Destruction Certificate In-House?
It might seem like a way to save a few bucks—destroying drives yourself and printing your own certificate. But from a legal and compliance perspective, this is a really bad idea. The real power of a hard drive destruction certificate comes from the independent, third-party verification it provides.
A self-made certificate just doesn't have the credibility to stand up to scrutiny in a legal fight or a formal audit. Auditors and lawyers want to see proof from a certified, unbiased expert who followed established industry standards, like those from NAID.
Using a professional, certified service like Reworx Recycling ensures the entire process is documented, defensible, and handled by trained pros. That independent validation is what gives the certificate its legal muscle and gives your organization true protection from liability. It shifts the burden of proof from your shoulders to a certified specialist who can vouch for the integrity of the whole process.
Ready to secure your data and strengthen your compliance strategy with audit-proof documentation? Partner with Reworx Recycling for certified, responsible, and socially impactful IT asset disposition. Schedule a pickup or donate your old equipment to help us build a more sustainable and equitable future while ensuring your business remains secure. Find out more at https://www.reworxrecycling.org/category/recycling-blog.